OT Security Has a New Owner: Now Manufacturing Must Make It Work
For decades, “security” on the plant floor meant safety, reliability, and throughput. Cybersecurity was often treated as an IT concern, until connectivity made it clear that modern manufacturing runs on converged systems. The same access that enables predictive maintenance, remote engineering, and faster changeovers also creates direct pathways for cyber incidents to disrupt production, compromise intellectual property, and ripple across the supply chain.
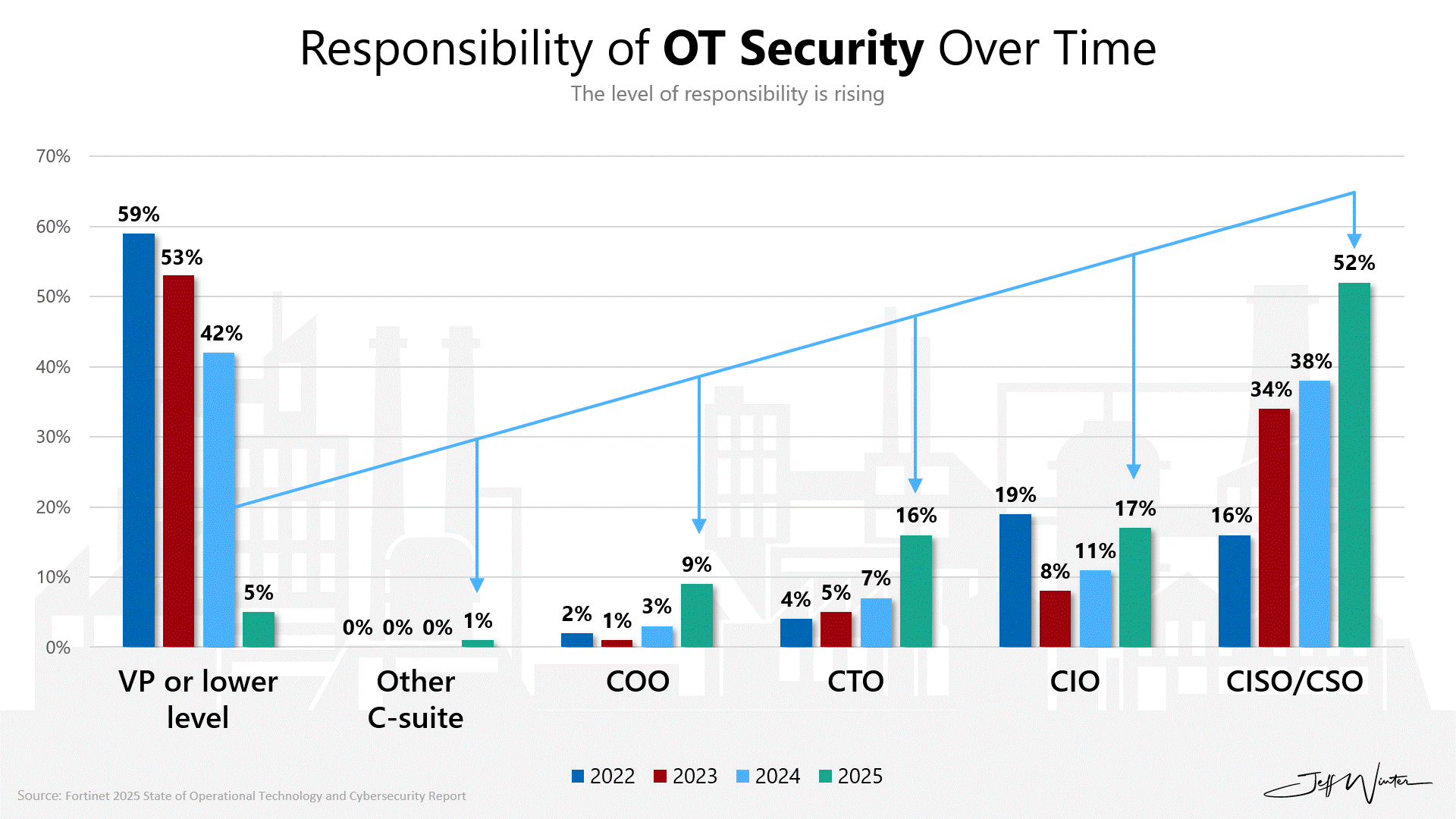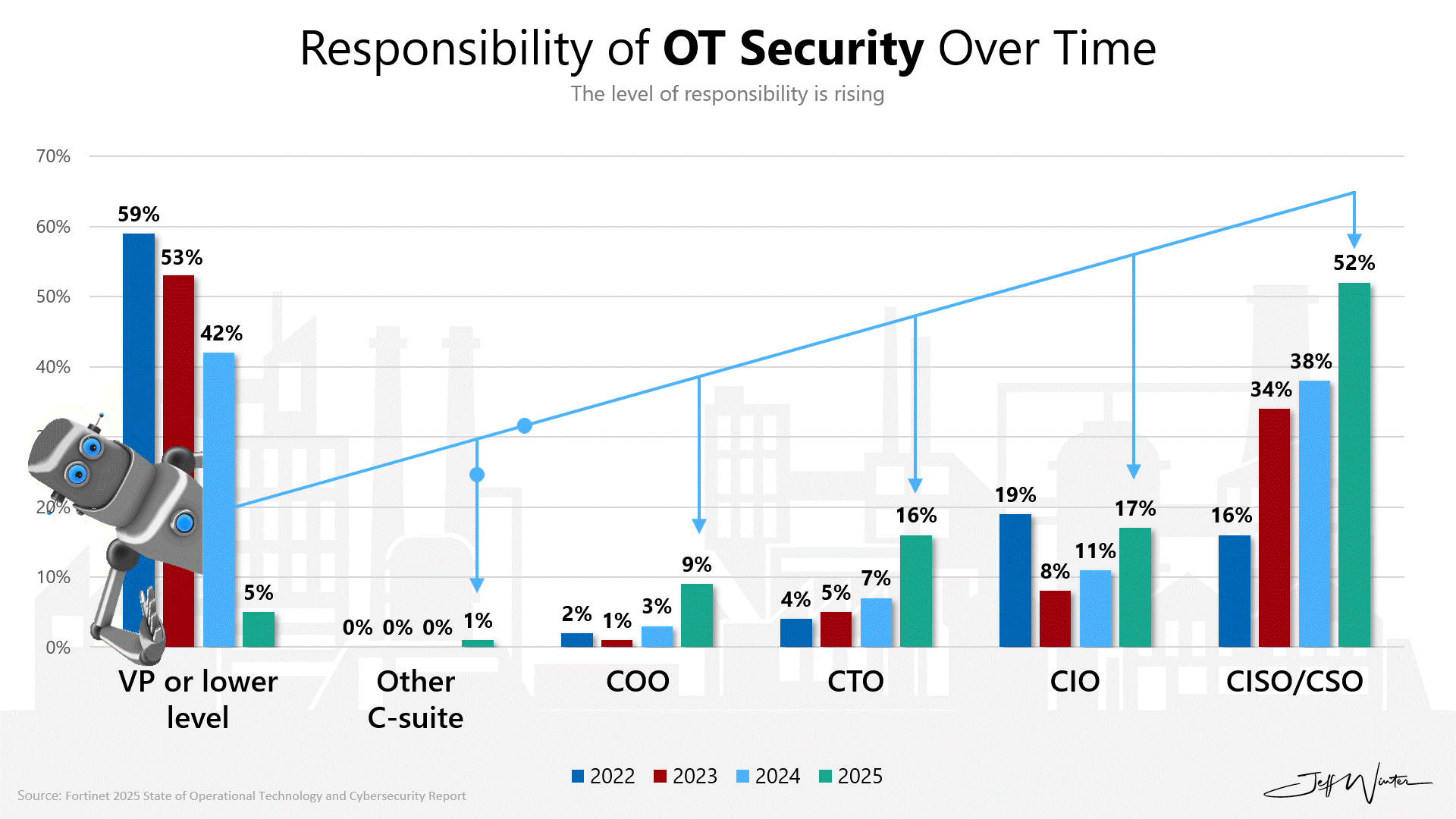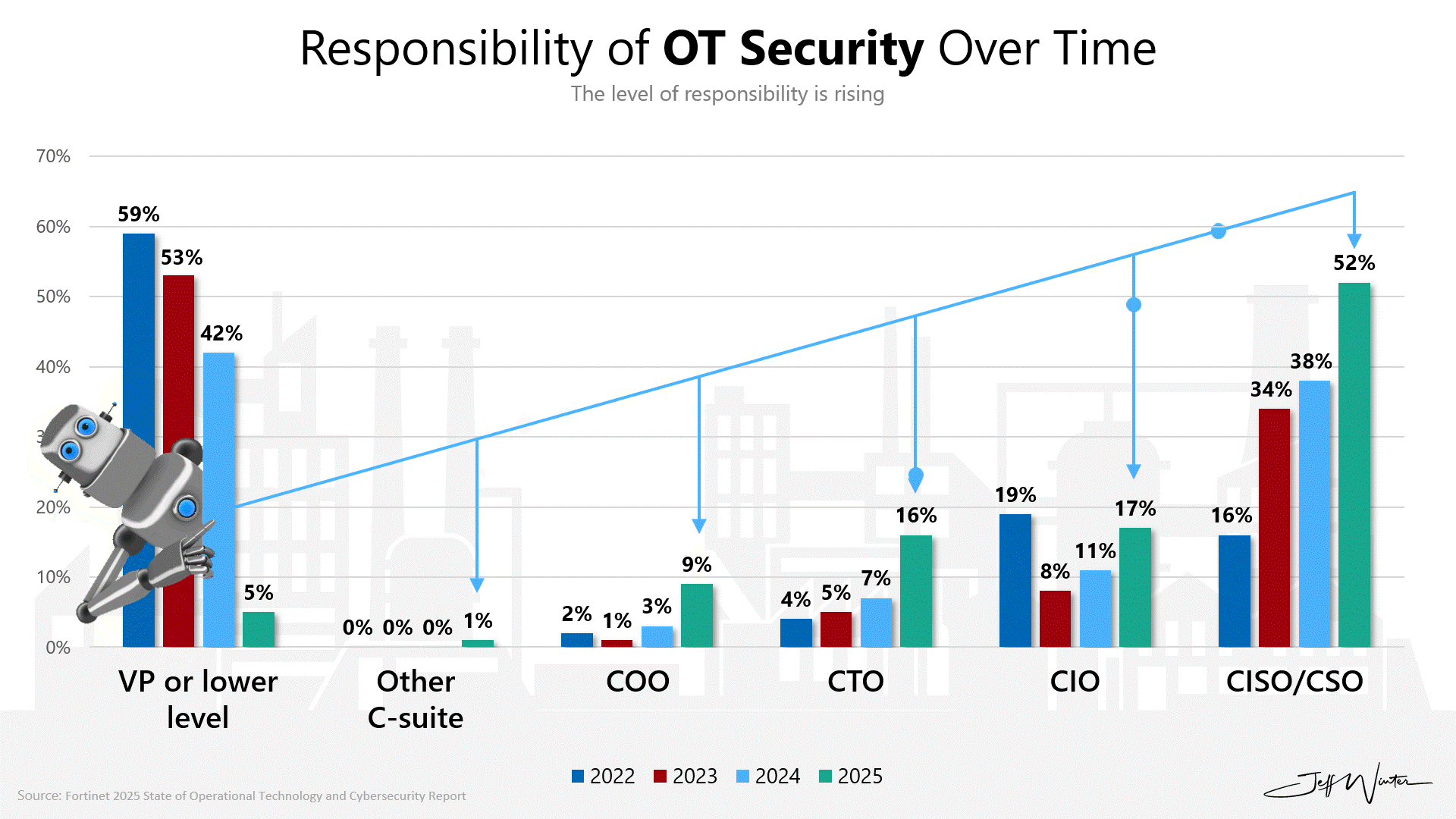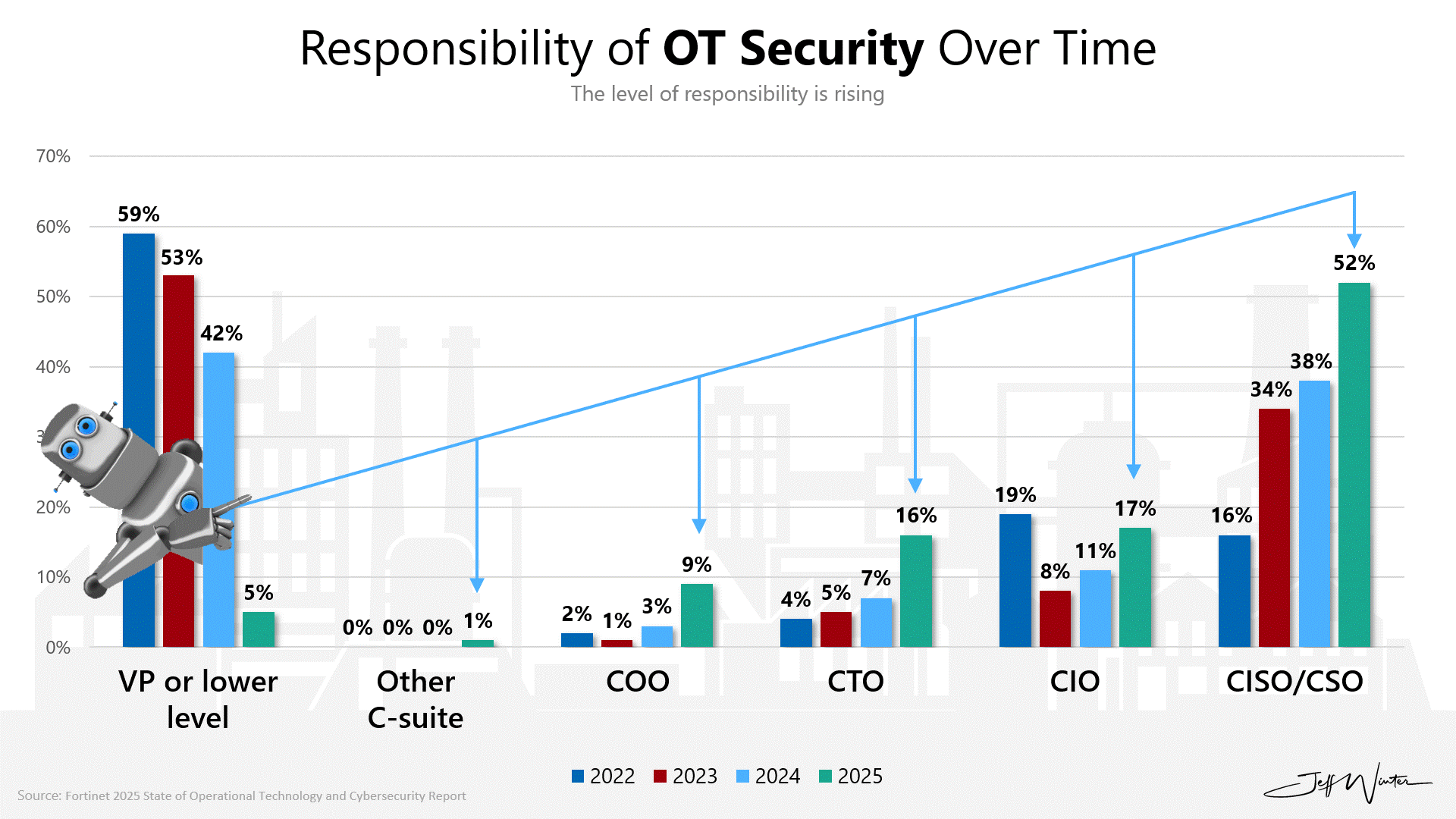
That is why ownership of operational technology (OT) security is migrating upward toward the CISO. Fortinet’s 2025 State of Operational Technology and Cybersecurity Report captures the shift showing how 52% of organizations now say their CISO/CSO is responsible for OT cybersecurity (up from 16% in 2022), and 80% expect OT cybersecurity to fall under the CISO/CSO within the next 12 months (up from 60%).
This elevation, in my opinion, is a huge positive development. It places OT cyber risk where enterprise risk belongs and makes it visible to executive leadership, connected to governance, and tied to business outcomes. But the organizational move only works if it is matched by an operating model that respects how factories run. OT security cannot be “copied and pasted” from IT without creating friction, delays, or unsafe workarounds.
Why manufacturing is in the crosshairs
Manufacturing is being targeted because it is operationally fragile in ways attackers can exploit.
Modern plants are optimized for efficiency, not interruption. Tight production schedules, high asset utilization, and limited tolerance for downtime create leverage that attackers understand very well. When production stops, decisions escalate quickly, often involving safety, customer commitments, and revenue exposure. That pressure shapes attacker behavior.
Verizon’s 2025 Data Breach Investigations Report identifies 3,837 security incidents in manufacturing, with 1,607 confirmed data disclosures. More importantly, the attack mix is changing. Malware now appears in 66% of manufacturing breaches, up from a historical range of 40% to 50%. This is not random activity. It reflects sustained focus on environments where malware can directly disrupt operations.
Ransomware continues to play a central role. Verizon also reports 47% of manufacturing breaches involved ransomware, which could be because manufacturing organizations are often unable to tolerate prolonged outages, and attackers are designing campaigns around that constraint.
What is more concerning is how these intrusions are enabled. Stolen credentials appear in 34% of breaches, vulnerability exploitation in 23%, and phishing in 19%, according to this same Verizon report. These are well-understood techniques. Their continued effectiveness suggests that access governance, vendor connectivity, and identity management remain weak points in many industrial environments.
However, the stat that caught my attention the most was seeing the rise in espionage. Verizon reports 20% of manufacturing breaches were espionage motivated, up from 3% the prior year. That shift matters. It indicates growing interest in intellectual property, process knowledge, supplier relationships, and production data. Manufacturing is no longer just a ransomware target. It is becoming a source of strategic information.
This aligns with IBM’s 2025 X-Factor Threat Intelligence Index Report, which shows that manufacturing accounted for 26% of incidents handled by its incident response teams, maintaining its position as the most targeted sector. Fortinet’s report, as a point of comparison, shows manufacturing represented 17% of ransomware victims, again placing it at the top of the list.
I believe the issue is not that manufacturing lacks cybersecurity awareness. It is that the consequences of failure are different. Cyber incidents in manufacturing rarely stay confined to IT systems. Fortinet reports 60% of organizations experiencing a cyber incident saw impacts across both IT and OT environments. That means ERP outages affect production scheduling, identity compromises affect plant access, and remote connectivity designed for efficiency becomes a pathway for disruption.
My view is pretty straightforward. Manufacturing is not lagging in cybersecurity maturity relative to other industries. It is simply exposed to a higher operational penalty when things go wrong. Downtime is not an inconvenience. It is a business event with safety, financial, and contractual consequences.
That is why manufacturing is targeted, and why cybersecurity in this sector cannot be treated as a supporting function. It is a core operational capability, and it explains why OT security is now being pulled into executive ownership rather than left at the plant level.
What changes when OT security reports to the CISO
When OT security moves under the CISO, the most important change is not technical. It is structural.
Risk becomes visible at the executive level. Funding decisions move out of annual plant budgets and into enterprise planning. Security is no longer justified as a local improvement but as a systemic requirement. That shift matters, and it explains why maturity metrics are moving in the right direction.
Fortinet’s data reflects this. 81% of organizations now self assess their cybersecurity process maturity at Level 3 or Level 4, and 49% report operating at the highest level of process maturity. Processes are being documented, standardized, and measured. Governance is improving. Reporting is becoming more consistent. From a leadership standpoint, this is real progress.
At the same time, 50% of organizations still experienced one or more OT security incidents in the past year, and that often raises the question of whether these maturity investments are actually working.
In my view, both things can be true at the same time.
As OT security elevates to the CISO, organizations gain visibility they did not previously have. Better monitoring, centralized logging, and OT aware detection increase the likelihood that incidents are identified and reported. In less mature environments, many incidents simply go unnoticed. Rising maturity often reveals risk before it reduces it.
There is also a timing effect. Governance and process maturity improve faster than technical reality. Documenting policies, defining standards, and integrating OT into enterprise security operations can happen in months. Re engineering networks, segmenting plants, modernizing access, and replacing legacy systems takes years. During that transition, exposure still exists.
The attack surface is also expanding faster than controls can be deployed. Connectivity continues to grow. Remote access is increasing. More systems are integrated into production workflows. Each efficiency gain introduces new pathways that must be secured. Maturity growth is real, but it is racing against structural complexity.
Another factor is attacker adaptation. Manufacturing has become a known pressure point. As organizations improve basic hygiene, attackers adjust techniques. Phishing becomes more targeted. Malware becomes more persistent. Credential theft focuses on trusted users and vendors. Incident volume does not drop simply because controls improve. It drops when operationally meaningful barriers are in place.
What reporting OT security to the CISO does change is how incidents are handled.
Organizations with higher maturity levels are seeing fewer severe outcomes. Fortinet reports 52% of organizations experienced zero intrusions in 2025, up from 6% in 2022, and 65% of organizations at the highest maturity level reported zero intrusions. When incidents do occur, recovery is faster and impact is lower. Operational outages impacting revenue declined to 42%, down from 52% the year before.
That distinction matters. The goal is not to eliminate incidents entirely. The goal is to prevent incidents from becoming operational crises.
CISO ownership helps shift the focus from reacting at the plant level to managing risk across the enterprise. It enables consistent architectures, shared playbooks, and coordinated response. But it also exposes the reality that cybersecurity maturity is not a switch. It is a multi year transformation that must keep pace with how manufacturing itself is evolving.
That is why rising maturity and persistent incidents are not a contradiction. They are a sign that organizations are finally seeing the full scope of the problem, and starting to address it at the right level.
What must change for CISO owned OT security to succeed
IT and OT convergence must be operational, not organizational
Moving OT security under the CISO fixes reporting lines. It does not fix behavior. Most organizations talk about IT OT convergence as if it were an end state, when in reality it is an operating discipline. True convergence means cybersecurity decisions are made with production consequences in mind and operational decisions are made with cyber risk in mind. That requires both sides to abandon some long held assumptions. IT teams often underestimate how fragile production environments can be under change. OT teams often underestimate how quickly a single access gap can scale into an enterprise wide problem. CISO ownership only works when those assumptions are surfaced and challenged in the same forum.
OT constraints must shape security design
OT does not behave like IT. Security strategies that assume otherwise tend to collapse under real plant conditions. Patch cycles are long, maintenance windows are scarce, and safety certifications restrict change. Many systems were never designed to be secured in the modern sense. In these environments, segmentation, compensating controls, and monitoring do more to reduce risk than chasing perfect hardening.
Access models are the fault line
Most OT security failures trace back to access. Not malware. Not exploits. Access.
OT systems are serviced by engineers, technicians, OEMs, integrators, and contractors whose access is episodic, urgent, and often tied to physical events. Traditional IT identity models assume stable users and predictable roles. That mismatch creates workarounds. Shared accounts persist. Vendor access becomes permanent. When that happens, the problem is not human behavior. It is a security design that does not reflect how work actually gets done.
Incident response must be built for production reality
IT incident response prioritizes containment. OT incident response must prioritize safety and continuity. That tension cannot be resolved during an incident. It has to be designed and rehearsed in advance. Playbooks must answer practical questions. What can be isolated. What must stay online. Who has authority to stop production. When those answers are unclear, incidents escalate through confusion rather than threat severity.
Metrics should make security uncomfortable
If OT security metrics make everyone feel good, they are probably wrong. Manufacturing does not care how many alerts were triaged. It cares how fast production was restored and how much damage was avoided. Recovery time, blast radius, and operational impact should dominate the scorecard. When those metrics are used, security becomes accountable to the business instead of just to itself.
References:
Fortinet. (2025). 2025 State of Operational Technology and Cybersecurity Report. Fortinet, Inc. https://www.fortinet.com/resources/white-papers/state-of-operational-technology-and-cybersecurity-report
Fortinet. (2025). 2025 Global Threat Landscape Report. Fortinet, Inc. https://www.fortinet.com/resources/reports/threat-landscape-report
Verizon. (2025). 2025 Data Breach Investigations Report. Verizon Business.
https://www.verizon.com/business/resources/reports/dbir/IBM Security. (2025). X-Force Threat Intelligence Index 2025. IBM Corporation.
https://www.ibm.com/reports/threat-intelligence